Session Hijacking Explained Session is broad technical term which can be used to refer to a state which is stored either on server side using in memory cache or on the client side using cookie local
Because default session is limited to the profile or instance profile used sometimes you need to use the custom session to override the default session configuration e g E seleniummon exceptions SessionNotCreatedException Message session not created probably user data directory is already in use please specify a unique value for
Session Hijacking Explained
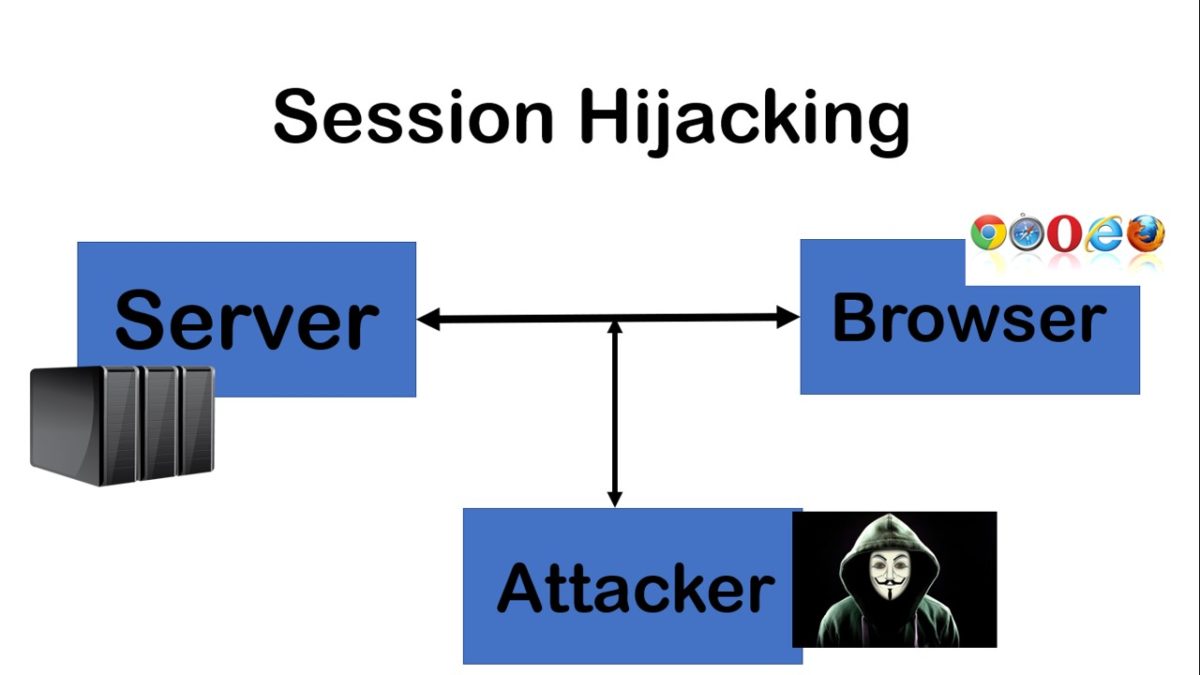
Session Hijacking Explained
https://allabouttesting.org/wp-content/uploads/2018/04/Session-Hijacking-cover-1200x675.jpg
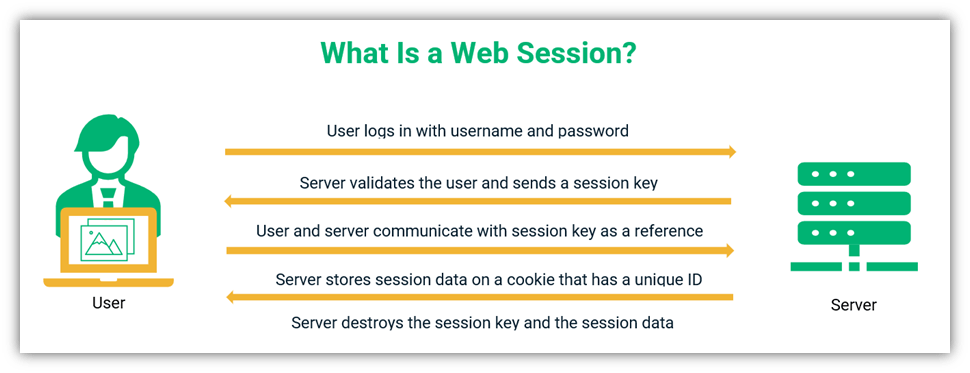
A Look At Session Hijacking Attacks Session Hijacking Explained
https://sectigostore.com/blog/wp-content/uploads/2021/10/what-is-a-session.png
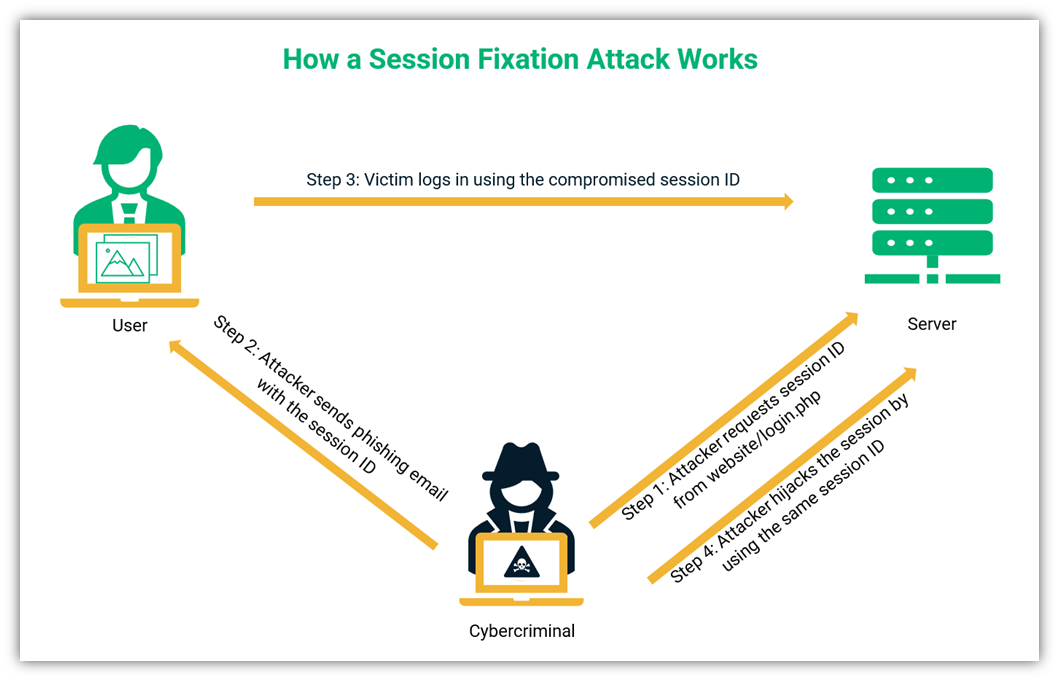
A Look At Session Hijacking Attacks Session Hijacking Explained
https://sectigostore.com/blog/wp-content/uploads/2021/10/how-session-fixation-works.png
To modify session data from the server after page creation you would need to use AJAX or even JQuery to get the job done Both of them can make a connection to the server Session Storage It is same like local storage date except it will delete all windows when browser windows closed by a web user In Session storage can store upto 5 mb data
Session Abandon destroys the session and the Session OnEnd event is triggered Session Clear just removes all values content from the Object The session with Terminates a session LOGOFF sessionname sessionid SERVER servername V VM sessionname The name of the session sessionid The ID of the session
More picture related to Session Hijacking Explained
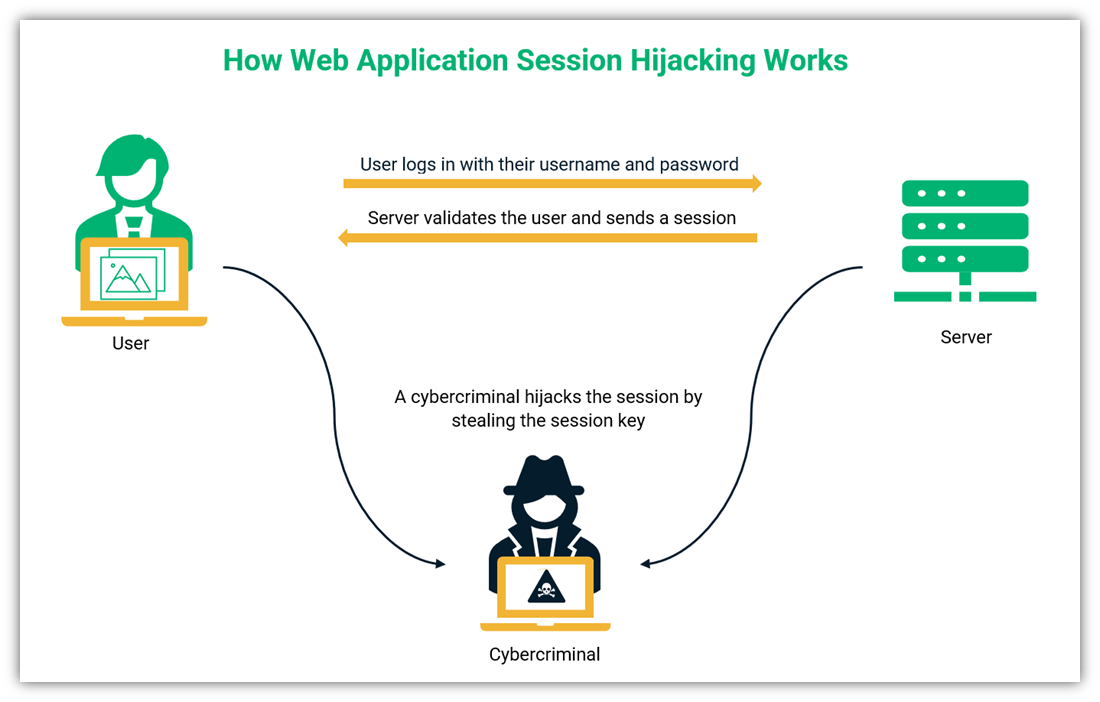
A Look At Session Hijacking Attacks Session Hijacking Explained
https://sectigostore.com/blog/wp-content/uploads/2021/10/how-session-hijacking-works.png

A Look At Session Hijacking Attacks Session Hijacking Explained
https://sectigostore.com/blog/wp-content/uploads/2021/10/session-hijacking-fun-illustration-1024x737.png
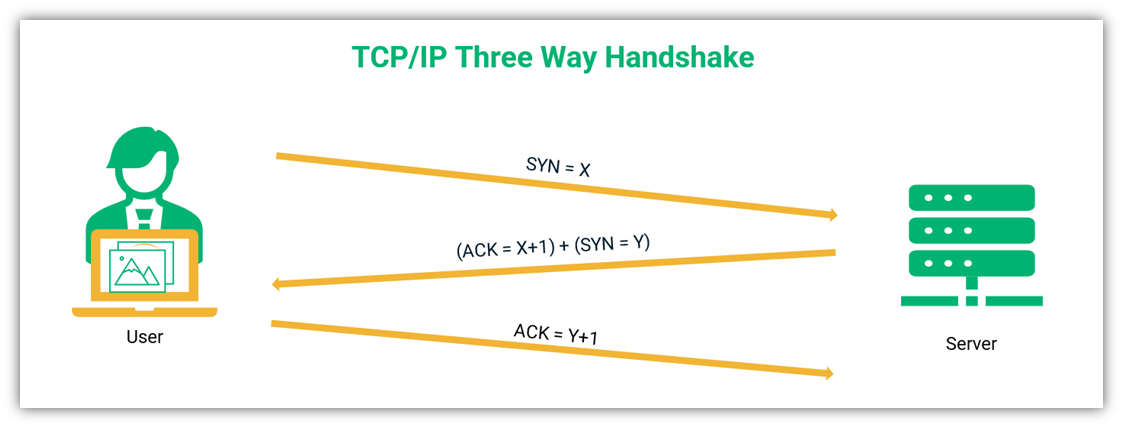
A Look At Session Hijacking Attacks Session Hijacking Explained
https://sectigostore.com/blog/wp-content/uploads/2021/10/tcp-ip-3-way-handshake.png
You can use the alter session set current schema B command to change the default schema to B so that when you say select from tbl it will translate it automatically to From here if the browser was manually opened then remote debugging can be used Start chrome with chrome remote debugging port 9222
[desc-10] [desc-11]

A Look At Session Hijacking Attacks Session Hijacking Explained
https://sectigostore.com/blog/wp-content/uploads/2021/10/session-hijacking-feature.jpg

The WKCR Hijacking Explained YouTube
https://i.ytimg.com/vi/0sAFXCti0vA/maxresdefault.jpg

https://stackoverflow.com › questions
Session is broad technical term which can be used to refer to a state which is stored either on server side using in memory cache or on the client side using cookie local

https://stackoverflow.com › questions
Because default session is limited to the profile or instance profile used sometimes you need to use the custom session to override the default session configuration e g

Session Hijacking Explained YouTube

A Look At Session Hijacking Attacks Session Hijacking Explained

Session Hijacking Explained In Cyber Security YouTube

Session Hijacking Explained shorts YouTube

What Are Session Tokens In Web Applications Session Hijacking

The Ultimate Threat DDoS DoS Sniffers And Session Hijacking Explained

The Ultimate Threat DDoS DoS Sniffers And Session Hijacking Explained

How Do Hackers Beat Multifactor Authentication Session Hijacking

Identipedia Authentication And Identity Concepts Explained

Session Hijacking GeeksforGeeks
Session Hijacking Explained - [desc-12]