What Are The Four Steps In The Information Security Risk Assessment Process Langsung aja deh tanpa banyak basa basi buat yg doyan ama JKT48 nih kumpulan foto Salkus para member JKT48 Silahkan dinikmati
Awal tahun 2018 di minggu pertama dunia Maya atau jagat internet di Indonesia di hebohkan dengan berita bocah viral dan wanita tua Awal kehebohan di mulai dari TOP5 APK ANDROID FOTO DAN VIDEO DEWASA BOKEP Sebelum lanjut membaca thread ini pastikan agan sudah berumur lebih dari 18 tahun ya karena konten
What Are The Four Steps In The Information Security Risk Assessment Process
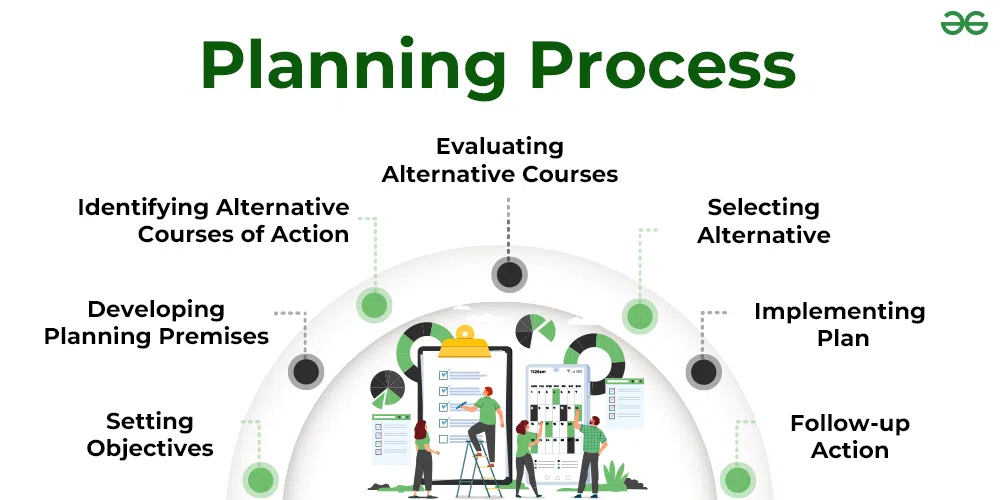
What Are The Four Steps In The Information Security Risk Assessment Process
https://media.geeksforgeeks.org/wp-content/uploads/20230331170143/planning-processs-copy.webp
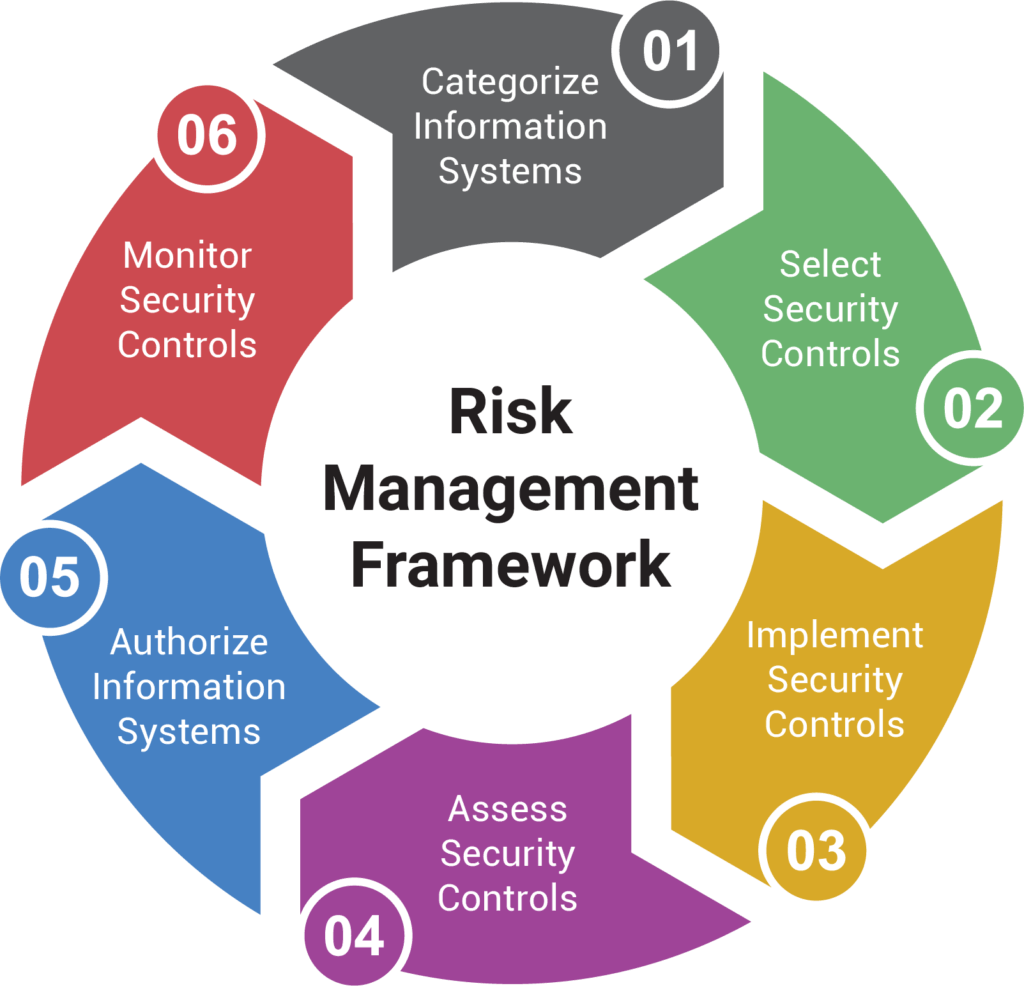
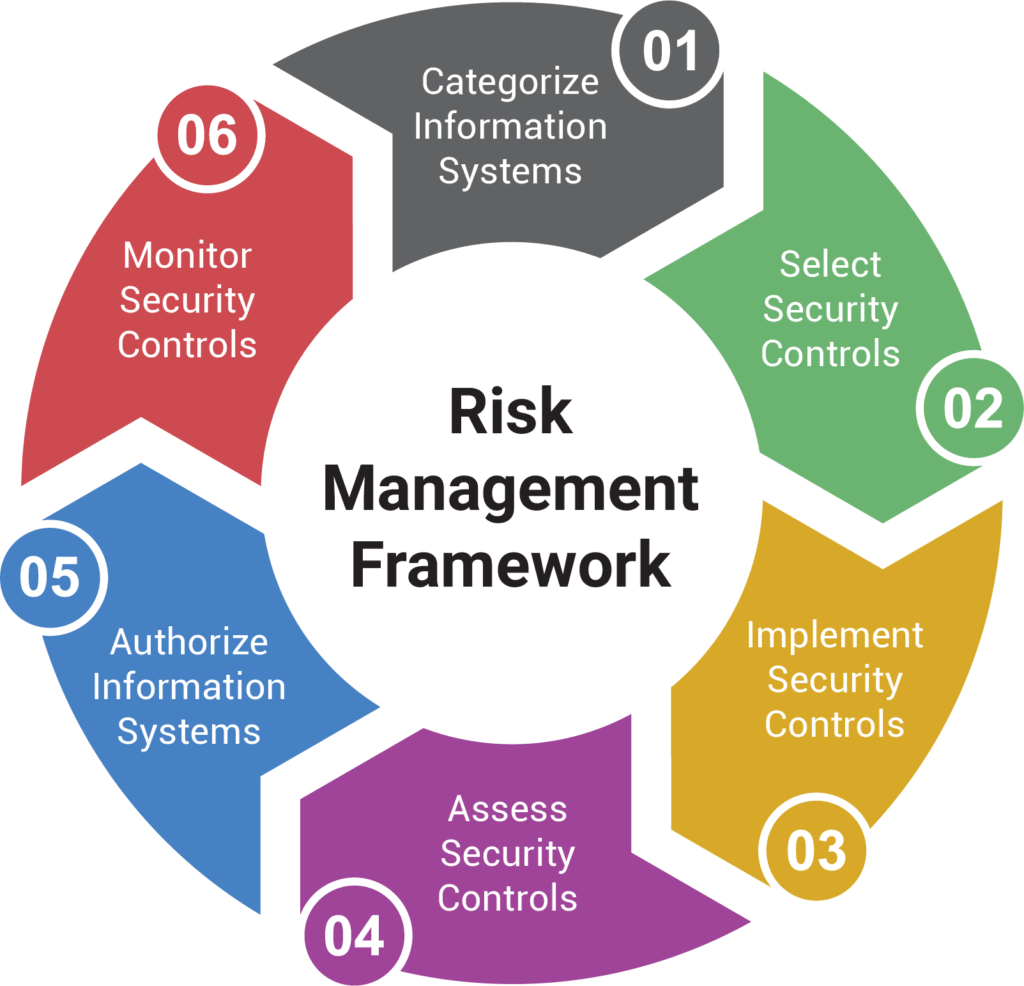
The Risk Management Framework
https://www.secjuice.com/content/images/2020/08/image-152.png

Risk Management Process Includes The Following
http://www.cmcco.com/Services/risk-management-process.png
Baru Heboh Lagi Video Bokep ASD Anak Kecil Dengan Perempuan Dewasa Salah Siapa Lah cowok aja nonton bokep Masa gue enggak Cowok mahhh wajar dung sist Biar pas malem pertama nggak salah tusuk Kamu mau kuping mu yang ditusuk bukan
Bagi penggemar video wekwek menonton video di platform Doodstream kemungkinan akan merasa jenuh jika hanya menonton satu video berulang ulang Tentu saja OME tv no SENSOR khusus 18
More picture related to What Are The Four Steps In The Information Security Risk Assessment Process

SECURITY RISK MANAGEMENT Threat Analysis Group
https://www.threatanalysis.com/wp-content/uploads/2022/02/Security-Risk-Assessment-v3-1-1024x768.png
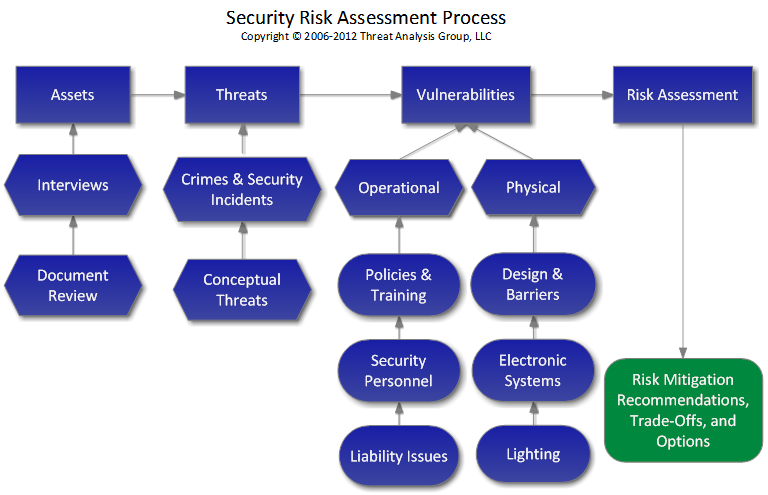
SECURITY RISK MANAGEMENT INDEPENDENT SECURITY CONSULTANTS
http://www.threatanalysis.com/wp-content/uploads/2015/05/Flow-Chart.png

Risk Assessment Process
https://www.alpinesecurity.com/wp-content/uploads/2020/02/Risk+Assessment+Process.jpg
Anak Kecil Baju Biru Viral Asli Ibu dan Anak Bikin Heboh Viral Video Video Ibu dan Anak Baju Biru Viral Asli FULL 10 menit Link video ibu dan anak baju biru Seiring berjalannya waktu be ef ini dilafazkan menjadi be ep kebiasaan orang indo f diganti p pada era tahun 80 an mulai ramai kata kata prokem bahasa gaul 80 an
[desc-10] [desc-11]

C mo Declara La Iglesia Que Alguien Es Santo Aqu Te Dejamos Una
https://i.pinimg.com/originals/2d/09/2c/2d092c70c5993db23496f1b5e04d7fdf.jpg

Risk Management Images
https://img.freepik.com/premium-vector/risk-management-process-diagram-vector-illustration_692379-262.jpg?w=2000

https://m.kaskus.co.id › thread
Langsung aja deh tanpa banyak basa basi buat yg doyan ama JKT48 nih kumpulan foto Salkus para member JKT48 Silahkan dinikmati
https://m.kaskus.co.id › thread › alamat-link-video-viral-tante-vs...
Awal tahun 2018 di minggu pertama dunia Maya atau jagat internet di Indonesia di hebohkan dengan berita bocah viral dan wanita tua Awal kehebohan di mulai dari
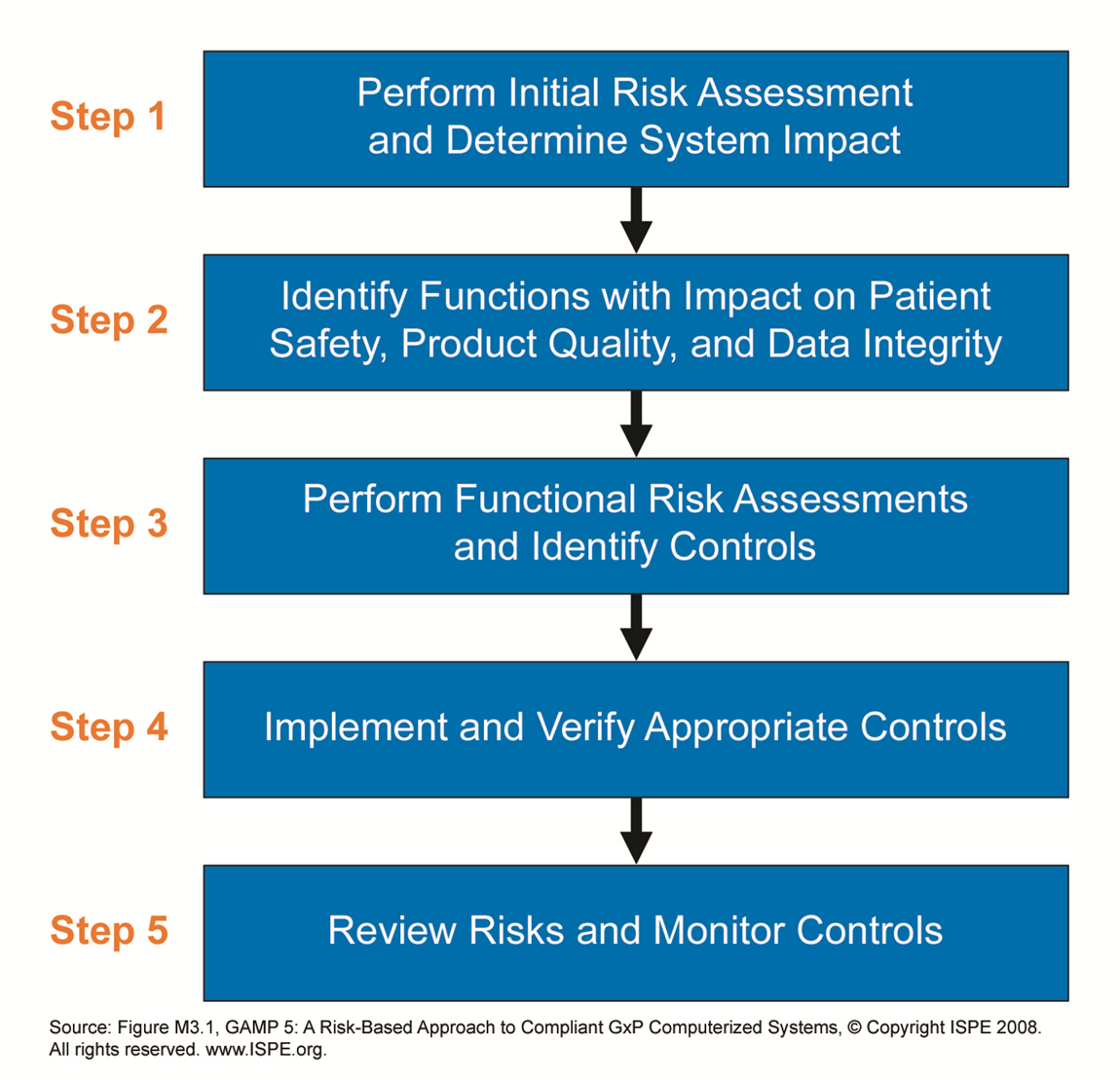
Risk Assessment

C mo Declara La Iglesia Que Alguien Es Santo Aqu Te Dejamos Una

What Is Risk Assessment Process
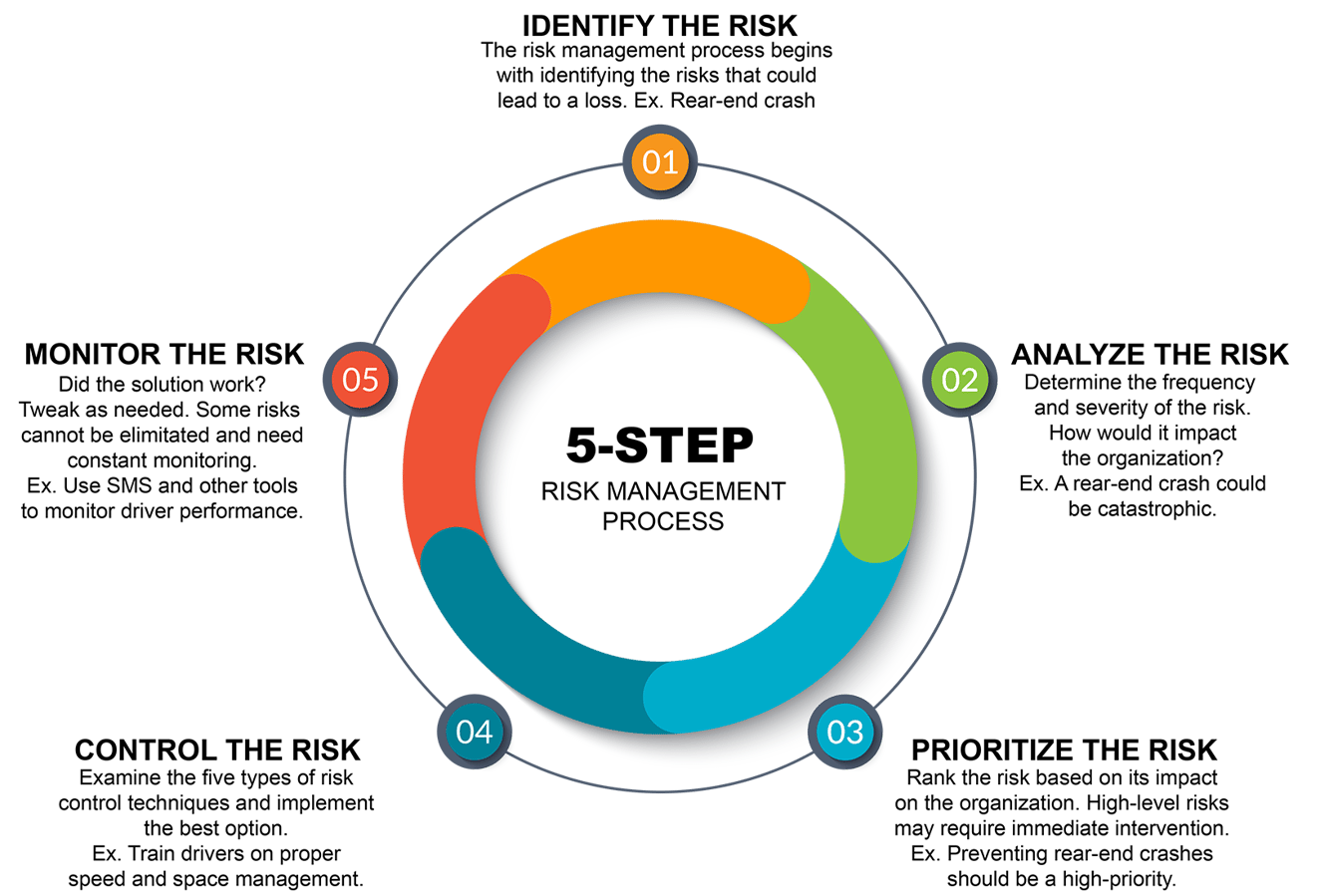
5 Steps Of Managing Risk Great West Casualty Company

Risk Management Process Security Analysis Methodology
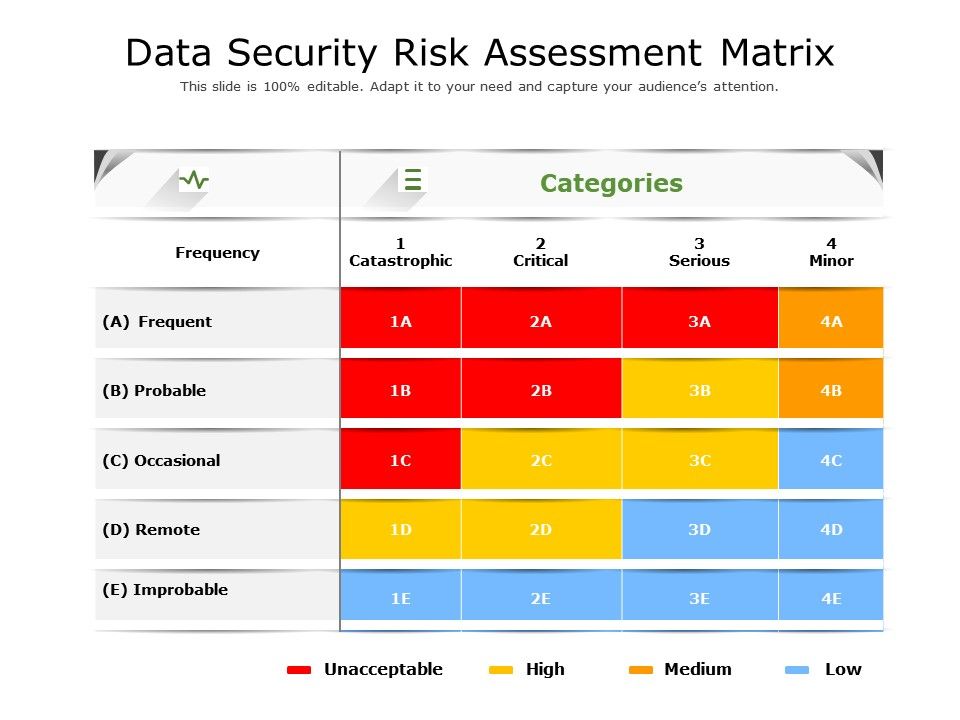
Data Security Risk Assessment Matrix Presentation Graphics

Data Security Risk Assessment Matrix Presentation Graphics

Deciding Company Name Process
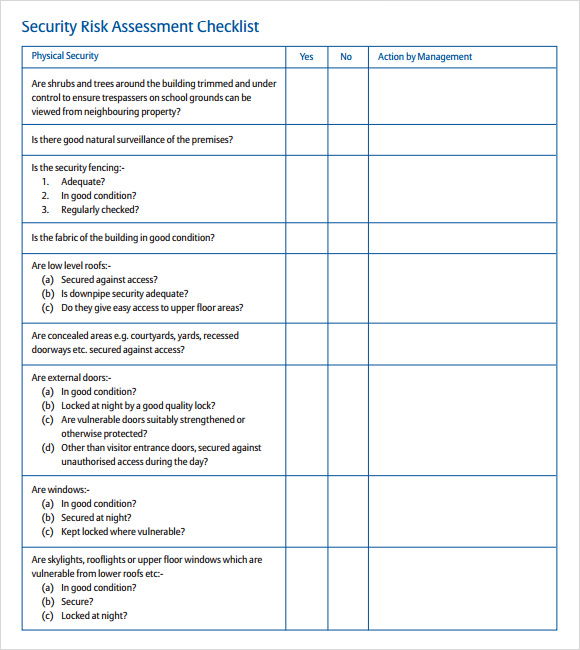
Security Questionnaire Template
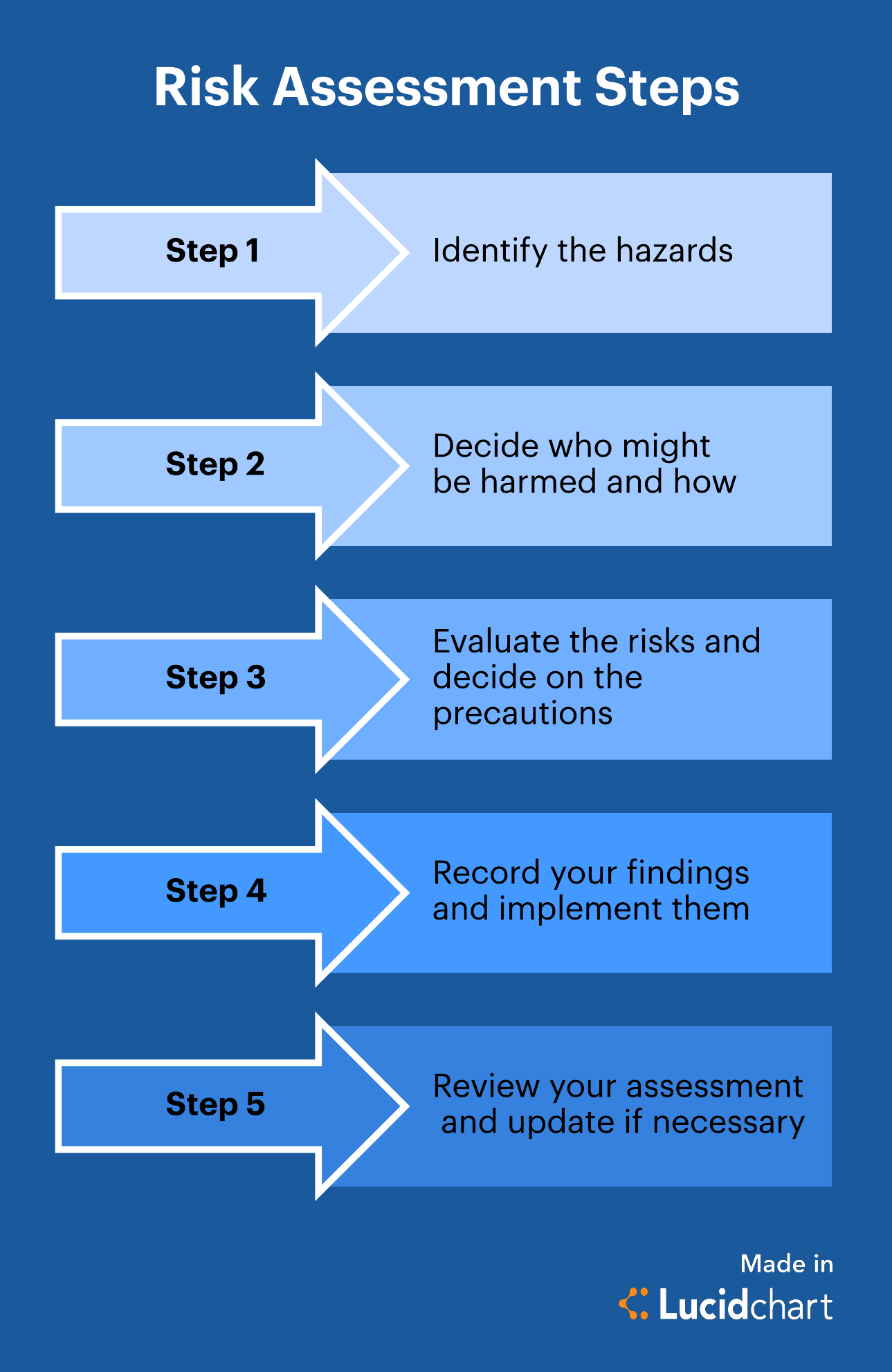
Diagram Risk Assessment Process Risk Assessment Process Diag
What Are The Four Steps In The Information Security Risk Assessment Process - OME tv no SENSOR khusus 18